At this moment in time, we are entirely dependent on businesses or services that either exist exclusively in the digital domain or are backed by digital channels. The senior executives of firms typically have worries such as the following: is it genuinely essential to have a website, and how risky is it to conduct business on our website?
We are able to see a tendency toward an increase in the number of cyberattacks as a result of the development in the number of enterprises that are present across the digital environment. Due to the fact that these attacks make business websites more vulnerable to further attacks and leave them at the mercy of the individuals who have hacked them, it is imperative that websites be protected.
What exactly is website security?
The technique of protecting a website from vulnerabilities such as malfunctions, phishing, cybercrimes, or cyberattacks is known as web security. The goal of web security is to prevent the loss of data that belongs to the company or its customers. It is always vital to undertake security testing on an internet site and scan it for faults in order to protect oneself against the thefts or losses that can be caused by digital hackers. This can be done by checking the website for vulnerabilities.

The information presented below provides a summary of web and cyber security: In the current climate, cyber security has emerged as the first line of defense; in addition, as the technological landscape continues to evolve, you will require continuous detection, monitoring, upgrades, and patches to protect yourself from potential threats.
The website’s security can be strengthened and protected against an invasion or attack by implementing a number of preventative measures and rules. This will make the website more secure. Elements of website security need to be implemented right from the start, and they must be thoroughly tested and kept up to date in order to remain effective in the face of ever-evolving threats brought on by advances in technology. When hackers or attackers target a website, the website will frequently become inaccessible or run more slowly, suffer a loss of traffic, and be stripped of vital customer information. In addition, hackers or attackers may steal client information.
What are the different kinds of threats to web security?
Due to a lack of appropriate website protection, some of the most typical sorts of dangers that can occur are as follows:
1. Malware is any piece of software that has been created with the explicit intention of interfering with, damaging, or gaining unauthorized access to a computer system.
2. Backlisting: If search engines find any malware on the website, it will be highlighted with an alarm that causes visitors to exit from your web page. Additionally, your site may be excluded from the web search page results. Backlisting can be avoided by regularly scanning your website for malware.
3. Exploits that take advantage of vulnerabilities Cybercriminals can gain access to your website and the information about your company that is stored on it by targeting vulnerable portions of a website and using an outdated plugin.
4. Defacement is a form of cyberattack that modifies the outward appearance of a website or a webpage. It is one of the four main categories of cyberattacks.
5. The risk of exposing sensitive data Hackers utilize software to send sensitive information via URLs, poorly designed code, and sessions, all of which increase the likelihood that the website is vulnerable.
6. Buffer Overflow: This vulnerability occurs when neighboring memory areas of the software are overwritten with data. This overwriting can be abused to introduce malicious code into the memory, which creates a vulnerability in the software that is being targeted.

When it comes to protecting web apps from malicious software, which may be injected into a website in order to steal data, reroute traffic, or even take over computer resources, there is a pressing need for web security, and this need should be met with a proactive strategy.
Keep in mind that the weaknesses will not only render your web application useless but will also result in a loss of reputation and a reduction in the number of users.
Your website and its users will be protected from harm if you put the following safety measures and best practices into practice. As a consequence, you will see a rise in both revenue and growth.
What can you do to make your website more secure?
If you are running a WordPress site, you should consider protecting your login site with WP Login LockDown plugin.
This plugin is a valuable security tool that helps safeguard your WordPress login page from unauthorized access attempts. By implementing WP Login LockDown, you add an extra layer of protection to prevent brute force attacks, where hackers attempt to guess your username and password repeatedly until they gain access.
WP Login LockDown works by limiting the number of login attempts from a specific IP address within a certain time frame. If someone exceeds the allowed number of failed login attempts, the plugin will temporarily block their IP address, effectively preventing further unauthorized login attempts. This feature helps protect your site from malicious individuals or bots trying to gain unauthorized access.
Additionally, WP Login LockDown provides you with various configuration options to customize the security settings according to your preferences. You can set the maximum number of login attempts, the duration of the lockout period, and even exclude specific IP addresses from being locked out. This flexibility ensures that you can strike a balance between security and user convenience.
By using WP Login LockDown, you not only enhance the security of your WordPress login page but also reduce the risk of unauthorized access to your site. This plugin is easy to install and configure, making it accessible even for users with limited technical expertise. Protecting your login site with WP Login LockDown is a proactive step in safeguarding your WordPress site and maintaining the privacy and integrity of your content and user data.
In order to make your website more secure, you should consider implementing these best practices in order to provide a safe web space both for yourself and your customers:
- SSL Certificate
Authenticating a website’s identity and establishing an encrypted connection are two of the functions of an SSL certificate. An encrypted connection between a web server and a web browser is made possible by the use of SSL, which stands for Secure Sockets Layer. In order to protect customers’ personal information and secure online transactions, businesses and organizations must install SSL certificates on their websites. In a nutshell, SSL protects data transport by encrypting it and preventing unauthorized parties from viewing or altering it. An SSL-protected website has a padlock icon next to its URL in the browser’s address bar.
We recommend!

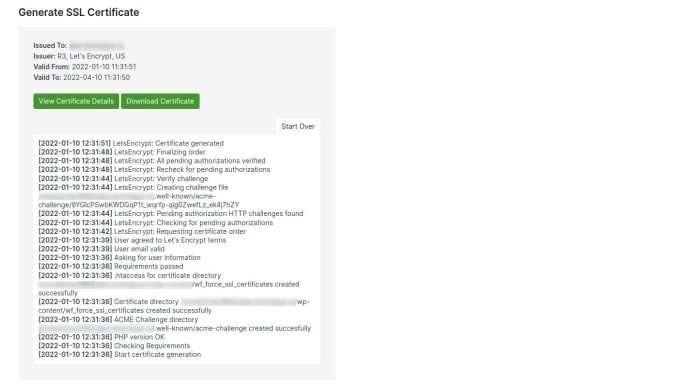
With WP Force SSL, the best WordPress SSL plugin on the market, users can easily redirect HTTP traffic to secure HTTPS and address SSL issues without the need to alter any code on their site. Using an SSL certificate, users can encrypt the entire website. It doesn’t matter if you use a Let’s Encrypt certificate or a purchased certificate from a third-party source; both will work. More than 14 SSL checks are included, as well as several other parameters aimed at providing the best possible service to the user. If you use WP Force SSL, you don’t have to make any changes to your existing themes or plugins. A notification is sent to the user when the certificate expires. Every page of your website is scanned by an integrated content scanner for potentially dangerous mixed content (https/http).
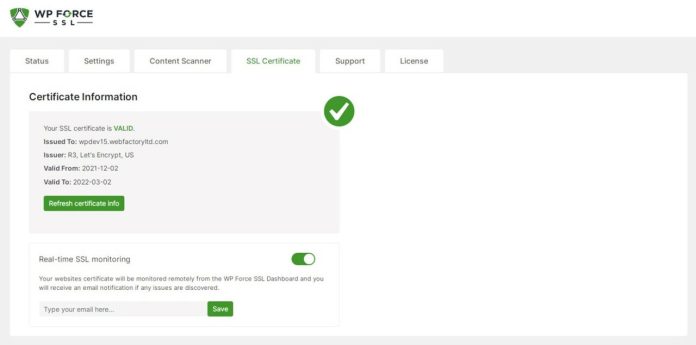
The plugin delivers a complete report after scanning all of your web pages in a matter of minutes if you wish to avoid difficulties with mixed material. More than 50 distinct problems are scanned for each time WP Force SSL runs a check to ensure your site is safe and secure. One dashboard lets you manage all your purchases and licenses, as well as your websites. Free and paid options are accessible to you in this regard.
Plugin’s key features are:
- The Content Scanner plugin checks every page on your site for mixed content in minutes.
- SSL real-time monitoring SSL monitor looks for more than 50 errors when scanning a user’s site. Easy-to-use and understand tools and options.
- Managing purchases, licenses, sites, and SSL monitors has never been easier.
- Developers answer most tickets, assuring the greatest assistance.
- Web application firewall (WAF): It protects websites from automated attacks that typically target less popular or smaller websites.
- Scanner for the website’s security: A scanner for the website checks it for vulnerabilities, malware, and other security concerns so that you can solve any issues that are found.
- SQL Injection: SQL injection allows for unauthorized access to the data and insights of a business, which ultimately leads to data breaches. Hackers will have access to the database as well as the authority to change, add to, or update the data in the database if they inject SQL code into it. As a result, it is preferable to prevent SQL injection in order to avoid security breaches on websites.
- Software updates: Websites that are hosted on a content management system (CMS) are at a greater risk of being compromised as a result of vulnerabilities and security flaws that are frequently detected in third-party plugins and apps. Installing regular updates to both the core program and plugins provides protection against these vulnerabilities.
- Protect your website by using HTTPS: The Hypertext Transfer Protocol Secure, or HTTPS, is a type of internet communication protocol that ensures the data exchanged between a user’s computer and a website is kept private and unaltered. The Transport Layer Security protocol, which gives three important layers of security, protects data that is delivered through HTTPS. These layers are as follows:
- Encryption is the process of encoding the data that is being transferred between parties in order to prevent snoopers from reading it.
- The integrity of the data means that it cannot be altered or corrupted while being transferred, either intentionally or accidentally, without it being discovered.
- Authentication serves to ward off attacks and foster trust among users, both of which are beneficial to a company’s operations in their own right.

- Integrated Single Sign-On and Multi-Factor Authentication for Secure Website:
- Single Sign-On, or SSO for short, is a sophisticated authentication method that streamlines the login process by granting access to various apps after a single sign-in.
- Using Multi-Factor Authentication (MFA), which stands for “Multiple Factor Authentication,” you are able to add an additional layer to the authentication process by combining login credentials with separate identification pieces.
- Due Diligence, Security Policies, and Firewalls to Prevent Cross-Site Scripting Attacks (XSS): When it comes to protecting a website from XSS attacks and other types of attacks, the solutions that are utilized most frequently include diligence, policies, and firewalls. Cross-site scripting is a technique that attackers employ to inject malicious code into online applications that are susceptible.
- XSS Attack: If any user is permitted to add content directly to your website, this will result in an XSS attack since a hacker will be able to directly inject harmful JavaScript into your website, which will lead to higher security risks.
- The consequences of losing data as a result of a catastrophic event should be understood by companies of all sizes, and secure backup and recovery procedures should be put into place. It is quite necessary for one to have a plan in place to get back up and running in the event that something unfortunate occurs.
- Web Application Firewalls: This helps you gain a handle over the internet traffic and their behavior by serving as a secure web gateway and protecting attacks, cross-site scripting, file inclusion, SQL injection, and a variety of other types of attacks.

By adhering to these best practices, your website will be protected from the following types of cyber threats:
- Theft of Data Hackers routinely attempts to steal sensitive information such as payment data, email addresses, and other specifics.
- Phishing: Phishing attacks will not only happen to email, but they will also happen to websites, where hackers will fool visitors into providing vital information by building a similar layout to that of the legitimate page. Redirects designed to harm:
- These kinds of attacks take people away from the website they plan to visit and send them to another website that is hostile. Session hijacking:
- These types of cyber/website attacks force visitors to take undesired actions on the site by taking over users’ sessions.
- Spam links and appealing comments can be placed on web pages to confuse visitors and direct traffic to dangerous websites. This practice is known as search engine optimization (SEO) spam.
Web security is the practice of protecting a website against vulnerabilities such as malfunctions, phishing, cybercrimes, or cyberattacks. When hackers or attackers target a website, the site will frequently become inaccessible or run more slowly. The website’s security can be improved and safeguarded against intrusion or attack by putting in place preventative measures.
In conclusion, I believe that you are now familiar with the concept of a secure website at this point. The methods that have been mentioned in the previous paragraphs are not only some of the easiest ways to secure your website from potential threats, but they are also some of the most effective. On the other hand, when it comes to safeguarding your website, you should never let your guard down, and you should never stop looking for ways to make it more secure.











Recent Comments