Every day, billions of users around the globe access websites that handle delicate personal information, such as login credentials, financial data, and private messages. To protect this data and ensure users are communicating with the correct website, the Internet relies on a critical piece of infrastructure — SSL CA Certificates. These certificates play a pivotal role in encrypting data and establishing trust between a user’s browser and a website.
Understanding how SSL CA certificates work is essential not only for developers and IT professionals, but also for everyday users concerned about their online security. The process, while technically complex, hinges on the fundamental concept of trust.
What is an SSL Certificate?
All Heading
An SSL (Secure Sockets Layer) Certificate is a digital certificate that authenticates a website’s identity and enables an encrypted connection. It is the cornerstone of HTTPS, the secure version of HTTP. When a website uses HTTPS, it means communication between the user’s browser and the server is encrypted using SSL or its successor, TLS (Transport Layer Security).
These certificates assure users that the website they’re visiting is indeed operated by who it claims to represent. Without this assurance, malicious actors could impersonate legitimate websites and trick users into sharing private information.
Enter the Certificate Authority (CA)
A Certificate Authority (CA) is a trusted organization responsible for issuing SSL certificates. CAs validate that the person or entity requesting a certificate genuinely controls the domain or organization in question.
The CA’s responsibility includes verifying the organization’s identity through various levels of checks, depending on the type of certificate requested. Once the checks are completed, the CA signs the certificate with a digital signature that browsers recognize as a mark of authenticity.

How Browsers Establish Trust
Web browsers maintain a trusted root store, which contains a list of root certificates from various recognized CAs. When a user visits a website, the browser checks the site’s SSL certificate and traces its signing authority back up the chain to one of the trusted root certificates.
This is known as the chain of trust. The certificate issued to the website is signed by an Intermediate CA, which in turn is signed by a Root CA. Here’s what happens in a simplified process:
- User types a web address, e.g., https://example.com.
- The website presents its SSL certificate to the browser.
- The browser verifies the certificate’s signature and checks that it was issued by a trusted CA.
- The connection is established if the certificate is valid, hasn’t expired, and matches the requested domain.
If any part of this process fails, the browser warns the user with a “Connection is not secure” message, discouraging them from proceeding.
Types of SSL Certificates
There are three main types of SSL certificates, each offering different levels of validation:
- Domain Validation (DV): Verifies domain ownership. Basic level of certification suitable for blogging sites or small businesses.
- Organization Validation (OV): Includes verification of the organization’s identity through official records. Often used by established businesses.
- Extended Validation (EV): Involves a rigorous vetting process. Activates the green address bar (in some browsers) and displays the company’s name — a visual indicator of a high level of trust.

How CA Certificates Help Prevent Attacks
Web-based threats often rely on deception. Attackers may create visually identical copies of legitimate websites to trick users into disclosing sensitive data. Without SSL certificates issued by a legitimate CA, these fake websites cannot spoof the same security signals, such as a valid HTTPS padlock in a browser.
Additionally, CA certificates help prevent man-in-the-middle attacks. In these attacks, a third party secretly intercepts and possibly alters communication. Encryption ensures that even if data is intercepted, it remains unintelligible without the session keys — secure elements enabled by SSL.
Revocation and Expiration
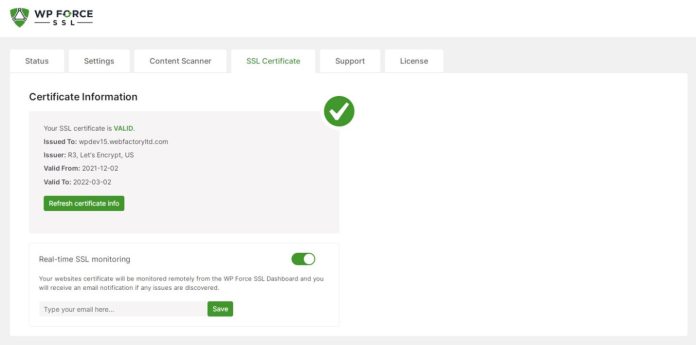
Sometimes, SSL certificates can become compromised or outdated. CAs provide mechanisms such as Certificate Revocation Lists (CRLs) and Online Certificate Status Protocol (OCSP) to allow browsers to check whether a certificate is still valid.
Moreover, SSL certificates are deliberately set to expire after a certain period, typically between 90 days and two years. This ensures that encryption keys are regularly rotated and that certificates are re-issued with updated identity validations.
The Move Toward Greater Encryption Adoption
Modern browsers increasingly enforce HTTPS connections. Many even display warnings when users visit unencrypted pages. This push has led to initiatives like Let’s Encrypt, a free, automated CA that provides DV certificates to promote widespread SSL adoption.
This trend reflects a broader movement toward making the Internet a safer space by default, where all websites — no matter how small — are expected to secure their users’ data.
Trust is the Foundation of Web Security
SSL CA certificates do more than just enable encryption — they verify authenticity. Without them, users would have no way of distinguishing between a trustworthy website and a potential trap.
For organizations managing websites, understanding and properly implementing SSL certificates is not just a best practice — it’s a necessity. For users, recognizing HTTPS and knowing what the padlock symbol means equips them with a greater ability to navigate the digital world securely.
The foundation of web security rests on trust — and this trust is built, maintained, and verified by SSL and Certificate Authorities working together in harmony.
Frequently Asked Questions (FAQ)
- What is the difference between SSL and TLS?
- SSL is the predecessor to TLS. TLS is the modern, more secure version of SSL that is used today, although the term “SSL” is still commonly used.
- How do I know if a website has a valid SSL certificate?
- Look for “https://” at the beginning of the URL and a padlock icon in the address bar. Clicking the padlock provides certificate details.
- Can SSL certificates be faked?
- Fraudulent certificates are extremely rare due to the secure verification processes of trusted Certificate Authorities. Browsers are also equipped to detect and block such certificates.
- What happens if an SSL certificate expires?
- When an SSL certificate expires, browsers display a warning, and the secure HTTPS connection is no longer trusted. Website owners must renew their certificates regularly.
- Is a free SSL certificate as good as a paid one?
- Free SSL certificates like those from Let’s Encrypt provide strong encryption. However, paid certificates may offer additional features such as extended validation and support services.










Recent Comments